ZeroDayGuard by DellferTM
Secure Your Embedded Device Firmware
In the digital age, device manufacturers and OEMs face increasing challenges to secure embedded device firmware against a myriad of cyber threats. Dellfer is here to support you with ZeroDayGuard, a certified developer toolkit and runtime service designed to safeguard your firmware and help you achieve the ultimate goal: perfect, secure code.
Seamless Integration, No Workflow Disruption
We know how important it is to maintain your workflow. That’s why ZeroDayGuard is designed to integrate seamlessly with your existing developer tools, requiring no changes to your current process. Remember, there is no one-size-fits-all solution to security. ZeroDayGuard is not just a product, but a comprehensive service that provides detailed forensics for developers.
Meet The Dellfer
Concierge Service
Our concierge service ensures a smooth and systematic integration of ZeroDayGuard technology into your firmware code. Here’s how it works:
1.
Installation
We install the toolset, perform various smoke tests to ensure the base platform is functioning in your developer environment.
2.
Dellferization
Dellferizing your firmware code involves analyzing the source code to determine its intended function, concurrently uncovering any issues in the legacy firmware code. Our step-wise integration mode ensures manageability, as instant protection of millions of lines of code is impractical. We do the hard work to give your code a deep cleaning.
3.
Issue Resolution
Despite many of our customers investing millions in cybersecurity, we consistently uncover numerous issues. These include cryptographic library vulnerabilities, data leak vulnerabilities, and unintentional inclusion of test code into production builds. Many issues are replicated due to copy-pasting, causing a single vulnerability to appear multiple times. Dellfer resolves all uncovered issues.
4.
Sustainable Development
Our build tools are designed to support developers in working efficiently while maintaining robust security going forward.

5.
Attack Detection
and Reporting
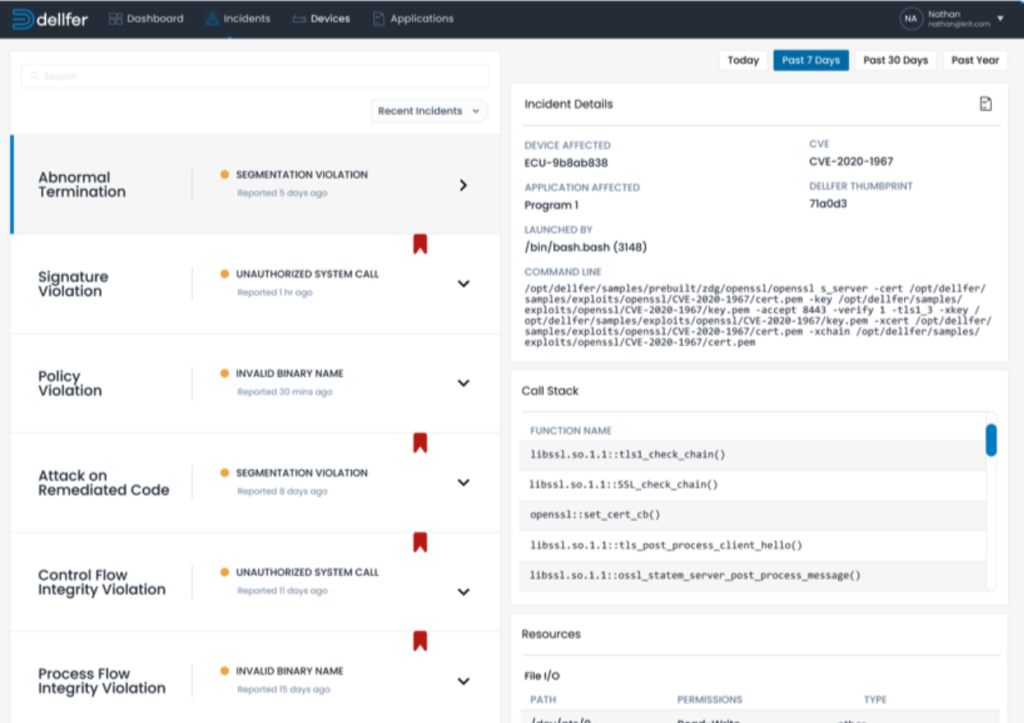
Any crash or remote code execution attack is detected and reported, providing crucial intelligence for issue resolution. When a new type of attack happens, the Dellferized code continues to run safely and reports each attempted incident, providing developers time to write and deploy the correct, optimal patch efficiently.
6.
Integration of Previous CVE Remediations
We also integrate detection for previously remediated Common Vulnerabilities and Exposures (CVEs).
7.
Device-Specific Service Setup
We establish a device-specific service that provides manufacturers with forensic details to address defects and vulnerabilities discovered in the field. This information can be shared with the firmware end user (the operator or admin of the device) as a threat intelligence service under a subscription. ZeroDayGuard guarantees no false positives, avoiding the inundation of end users and developers with false alarms.
8.
Training and Updates
Throughout the entire process we keep you up to date on the process and vulnerabilities uncovered. Additionally, we provide training on our technology and on the vulnerabilities uncovered and the remediations applied.
Empower Your Development
with ZeroDayGuard
In a world where cybersecurity is paramount, Dellfer’s ZeroDayGuard provides a comprehensive and methodical approach to fortifying your embedded device firmware. Let us help you reach your perfect code destination, free from vulnerabilities and fortified against attacks. Contact us today to start your journey towards a more secure future for your devices and end users.

